Privileged accounts are the keys to your organization’s most critical systems and sensitive data. While these accounts enable essential operations, they also represent a major security risk if mismanaged. Cyber attackers know that compromising privileged credentials can provide unrestricted access to your infrastructure.
For that reason, PATECCO has compiled a list of the most common privileged access risks and effective solutions to help organizations protect their critical systems, reduce security threats, and maintain compliance with industry regulations.
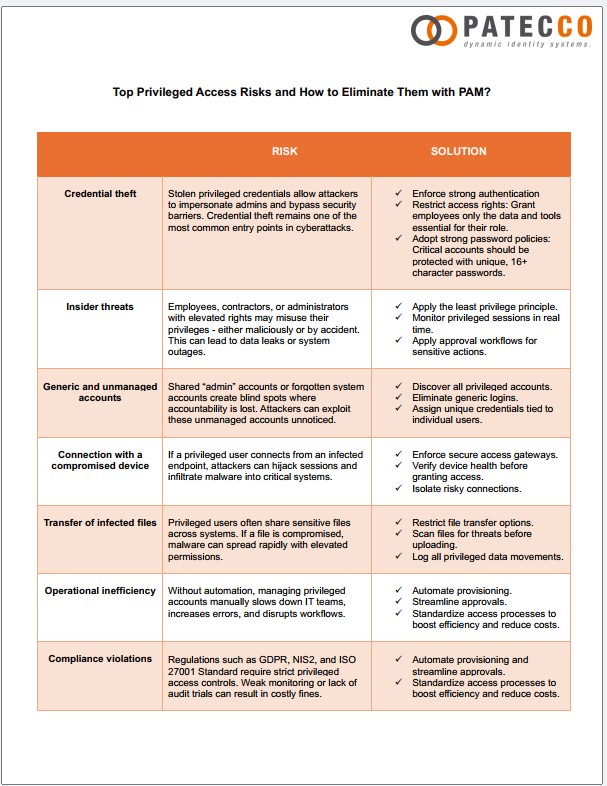
1. Credential theft
- The risk:
Stolen privileged credentials allow attackers to impersonate admins and bypass security barriers. Credential theft remains one of the most common entry points in cyberattacks.
- The solution:
Organizations can mitigate this risk by enforcing strong authentication. Access rights should be restricted so that employees only have the data and tools essential for their role. Critical accounts should also be protected with unique passwords of at least 16 characters.
2. Insider Threats
- The risk:
Employees, contractors, or administrators with elevated rights may misuse their privileges – either maliciously or by accident. This can lead to data leaks or system outages.
- The solution:
To mitigate insider threats, organizations should apply the least privilege principle, monitor privileged sessions in real time, and implement approval workflows for sensitive actions to ensure that all high-risk operations are properly authorized and auditable.
3. Generic and Unmanaged Accounts
- The risk:
Shared “admin” accounts or forgotten system accounts create blind spots where accountability is lost. Attackers can exploit these unmanaged accounts unnoticed.
- The solution:
Organizations should identify all privileged accounts, eliminate generic or shared logins, and assign unique credentials tied to individual users to ensure accountability and reduce the risk of undetected access.
4. Connection with a Compromised Device
- The risk:
If a privileged user connects from an infected endpoint, attackers can hijack sessions and infiltrate malware into critical systems.
- The solution:
To mitigate this risk, organizations should enforce secure access gateways, verify device health before granting access, and isolate risky connections to prevent compromised endpoints from affecting critical systems.
5. Transfer of Infected Files
- The risk:
Privileged users often share sensitive files across systems. If a file is compromised, malware can spread rapidly with elevated permissions.
- The solution:
To mitigate this risk, organizations should restrict file transfer options, scan all files for threats before uploading, and log all privileged data movements to ensure traceability and prevent the spread of malware.
6. Operational Inefficiency
- The risk:
Without automation, managing privileged accounts manually slows down IT teams, increases errors, and disrupts workflows.
- The solution:
Organizations can improve efficiency by automating provisioning, streamlining approval processes, and standardizing access procedures, which helps reduce errors, speed up operations, and lower costs.
7. Compliance Violations
- The risk:
Regulations such as GDPR, NIS2, and ISO 27001 Standard require strict privileged access controls. Weak monitoring or lack of audit trials can result in costly fines.
- The solution:
To mitigate compliance risks, organizations should automate provisioning, streamline approval workflows, and standardize access processes. These measures help ensure consistent enforcement of policies, maintain regulatory compliance, and reduce the likelihood of violations.
Why PAM Matters?
Privileged Access Management does more than protect accounts – it strengthens compliance, enhances operational efficiency, and reduces security risks. By providing full visibility into privileged activities, PAM helps organizations detect anomalies before they escalate into breaches. It also enforces consistent access policies across all systems, reducing human error and minimizing insider threats. Organizations that implement PAM effectively gain control, accountability, and resilience, turning privileged access from a vulnerability into a strategic advantage.
How PATECCO Turns Risk into Resilience?
Privileged access risks can pose serious threats to your organization’s critical systems, data, and compliance posture. PATECCO brings extensive expertise in PAM to help organizations transform these risks into operational resilience. Our approach ensures that privileged accounts are secured, monitored, and managed efficiently, allowing teams to focus on growth and innovation. By choosing PATECCO, you gain professional support in the following areas:
- Identifying and securing all privileged accounts for full visibility and control.
- Seamless integration with existing IAM systems.
- Ensured compliance with industry regulations through comprehensive monitoring, audit and controls.
- Providing proactive monitoring and support to detect and respond to threats in real time.
Click on the image, to open the PAM one-pager:
If your organization is looking for a trusted IAM partner to enhance your cybersecurity resilience and support scalable, long-term compliance, don’t hesitate to get in touch with us. We are here to help you turn information security into a true business advantage.

