Digital transformation offers enormous opportunities for businesses, but at the same time it brings growing risks. Cybercriminals are using increasingly sophisticated methods to steal data, disrupt business processes, or demand ransom payments. To effectively counter these growing threats, new concepts are needed: Zero Trust as the core principle of cybersecurity and Artificial Intelligence (AI) as intelligent support. Together, they form a powerful alliance that makes organizations more resilient against attacks.
How Companies Can Strengthen Their Defenses with Zero Trust and Artificial Intelligence
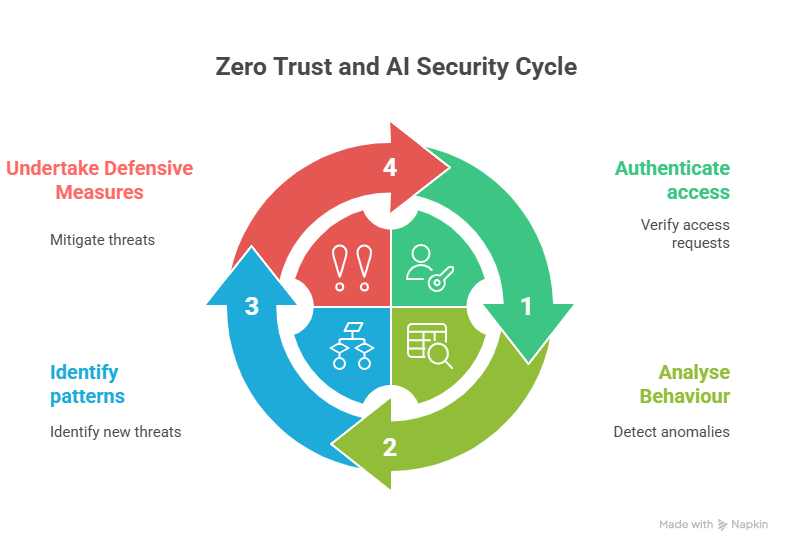
Zero Trust is based on the principle of “Never trust, always verify“. Every access attempt, whether from within the internal network or from outside, must be authenticated and authorized. This approach reduces the risk that attackers can move unnoticed within systems.
AI takes this approach a step further. It analyzes countless data points, detects anomalies, and can even identify previously unknown attack patterns. Instead of relying on manual checks, organizations benefit from automated processes that respond faster and more precisely.
Why the Combination of Zero Trust and AI Sets New Standards in Cybersecurity
Zero Trust creates a strong security architecture by eliminating unrestricted access and strictly controlling user rights. However, a purely rule-based system can quickly reach its limits in the face of dynamic attack scenarios. AI complements this framework with its ability to learn from patterns and continuously evolve.
This means that attacks can not only be prevented but also detected in real time. AI enables contextual risk assessment – by considering factors such as a user’s location, behavior, and device profile. As a result, the security strategy becomes adaptive and flexible.
Access Management as the Core of Modern Zero Trust Strategies
At the heart of every Zero Trust strategy lies effective access management. It determines who is allowed to access data, systems, and applications, under which conditions, and at what time. Instead of relying on broad access rights or one-time approvals, the principle is clear – every access request is continuously verified and granted only with proven legitimacy. This prevents compromised accounts or devices from becoming gateways for attacks.
AI significantly enhances this approach. By analyzing user behavior, contextual data, and risk factors, access management can be dynamically adapted. For example, an employee suddenly trying to access sensitive data from an unusual location or at an unusual time is automatically subject to stricter checks or temporarily blocked. In this way, a scalable and resilient system is created that combines security with user-friendliness.
Zero Trust Meets Artificial Intelligence – A Security Concept for the Future
The future of cybersecurity will be influenced by intelligent, adaptive solutions. Zero Trust provides the foundation – clear rules, strict access controls, and an uncompromising stance toward trust. AI complements this model with the ability to continuously evolve and proactively identify threats.
This combination not only makes organizations more secure but also more resilient. They can respond more quickly to changes, meet regulatory requirements, and offer their customers the assurance that data and systems are reliably protected. Organizations that adopt this combination gain more resilience, trust, and competitiveness. In a world where cyberattacks are no longer the exception but the rule, this level of preparation determines the difference between success and failure. Zero Trust and Artificial Intelligence are the next logical step in the evolution of cybersecurity.
If your organization is looking for a trusted IAM partner to enhance your cybersecurity resilience and support scalable, long-term compliance, don’t hesitate to get in touch with us. We are here to help you turn information security into a true business advantage.

