Zero Trust has become the standard for modern security – never trust, always verify. Many organizations focus on tools like firewalls, network segmentation, and multi-factor authentication – but the real foundation often goes unnoticed: Identity Governance and Administration (IGA). IGA goes beyond simply managing who can log in; it ensures the right people have the right access at the right time. By providing clear visibility, enforcing access policies, and continuously monitoring risk, IGA turns the Zero Trust concept from a theory into a practical, enforceable strategy. Without it, even the strongest security tools can fall short.
Why Zero Trust Starts with Identity?
The concept of Zero Trust is simple: no one is automatically trusted, even inside your network. Every request must be verified, every access point evaluated, and every identity treated as potentially risky. Simple in theory, but impossible to execute without strong identity governance.
Too often, organizations focus on tools like multi-factor authentication or network segmentation. The real work happens at the identity layer: Who has access? What can they do? Should they still have that access? Without answers, the rest of Zero Trust becomes fragile. Identity isn’t just a checkpoint – it’s the foundation that keeps policies consistent, reviews on schedule, and risk signals flowing to the right places. If trust must be earned continuously, it all starts with identity.
How Identity Governance Powers Zero Trust?
Every effective Zero Trust approach begins with a simple principle: you can’t secure what you can’t see. Identity Governance provides that clarity, revealing who has access, where it leads, and whether it’s still appropriate.
In most organizations, access grows quickly. Employees join, change roles, or leave, and each change adds new permissions. Over time, these privileges accumulate, creating complexity and risk. Identity Governance brings structure to this chaos, defining who should have access, under which conditions, and for how long.
By connecting users, roles, and systems, Identity Governance becomes the foundation of Zero Trust. It introduces accountability at every level – from employees and contractors to service accounts and automated bots – ensuring consistent enforcement of least privilege, real-time visibility, and fewer blind spots. When Identity Governance and Zero Trust work in tandem, access control stops being reactive. It becomes a dynamic system that adapts automatically as users, roles, or risk factors change.
The Role of Identity Governance in Strengthening Zero Trust
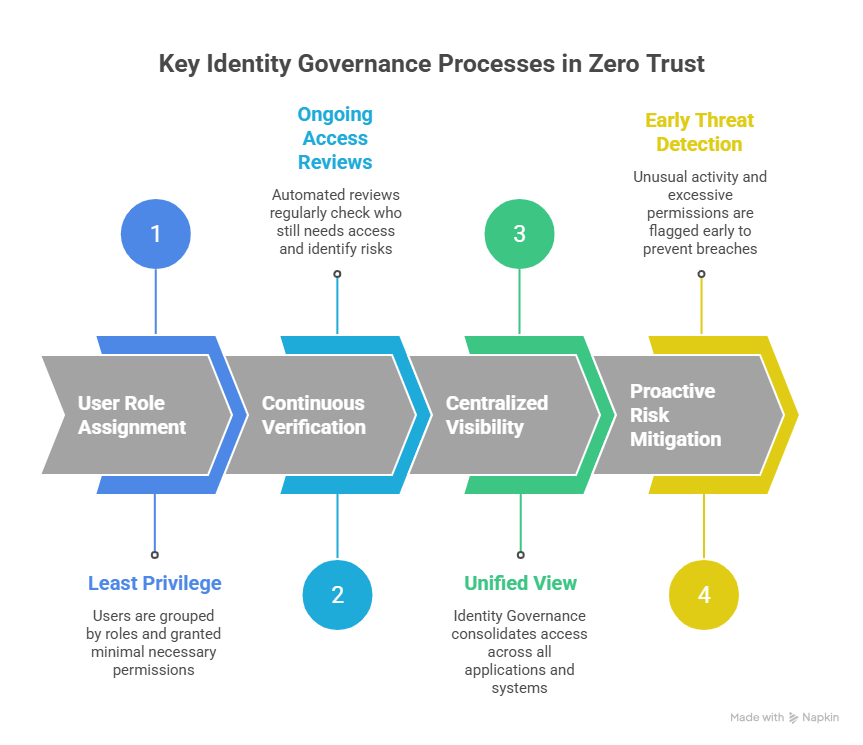
- Applying the Principle of Least Privilege
Zero Trust only works when access is limited. Every user should see and do only what’s necessary. Identity Governance makes this possible by grouping users by roles and granting permissions accordingly – transparent, fair, and easy to track. When someone changes roles or completes a task, their access updates automatically. No forgotten accounts, no open doors. Regularly pruning permissions keeps systems secure and reduces data exposure. - Continuous Verification and Access Monitoring
Trust isn’t permanent – it must be continually earned. Identity Governance ensures verification happens automatically. Ongoing access reviews identify who still needs access, who doesn’t, and where potential risks lie. Instead of waiting for yearly audits, problems surface early, quietly and reliably – far more effective than manual tracking. - Full Visibility Across Users and Applications
Modern organizations rely on countless apps and systems. Without centralized oversight, tracking who has access to what is nearly impossible. Identity Governance consolidates these connections into a single view, showing exactly who can access which systems. This clarity helps security teams detect unusual activity, validate policies, and respond quickly to threats. - Lower Insider Risk and Breach Exposure
Many breaches occur because users have excessive access. Identity Governance reduces this risk by continuously reviewing permissions and flagging unusual activity early. When employees change roles or leave, their access is updated immediately. The focus isn’t suspicion – it’s precision: ensuring people have exactly the access they need and nothing more.
Identity Governance not only complements Zero Trust but also strengthens it. By improving visibility, reducing risk, and enabling automation, it transforms security into a continuous, dependable process. Modern identity governance solutions must establish strong access controls from the start, particularly by enforcing the principle of least privilege. To support a true Zero Trust approach, identity governance should connect seamlessly with complementary tools such as privileged access management (PAM) and identity and access management (IAM), ensuring a unified and coordinated security framework.
PATECCO provides a proven identity governance approach that guides organizations in deploying, integrating, and maintaining modern governance capabilities. By aligning governance processes with existing security ecosystems, PATECCO helps organizations strengthen access control, streamline operations, and advance toward a mature Zero Trust model.
