Managing digital identities throughout their entire lifecycle is a cornerstone of effective identity security. The Joiner-Mover-Leaver (JML) process ensures that user access is continuously aligned with an individual’s role within the organization. As employees join, change positions, or leave, their access rights must be granted, adjusted, or revoked in a timely and controlled manner. When implemented correctly, a well-structured JML process strengthens security, supports regulatory compliance, and minimizes operational risk.
Understanding the JML Process
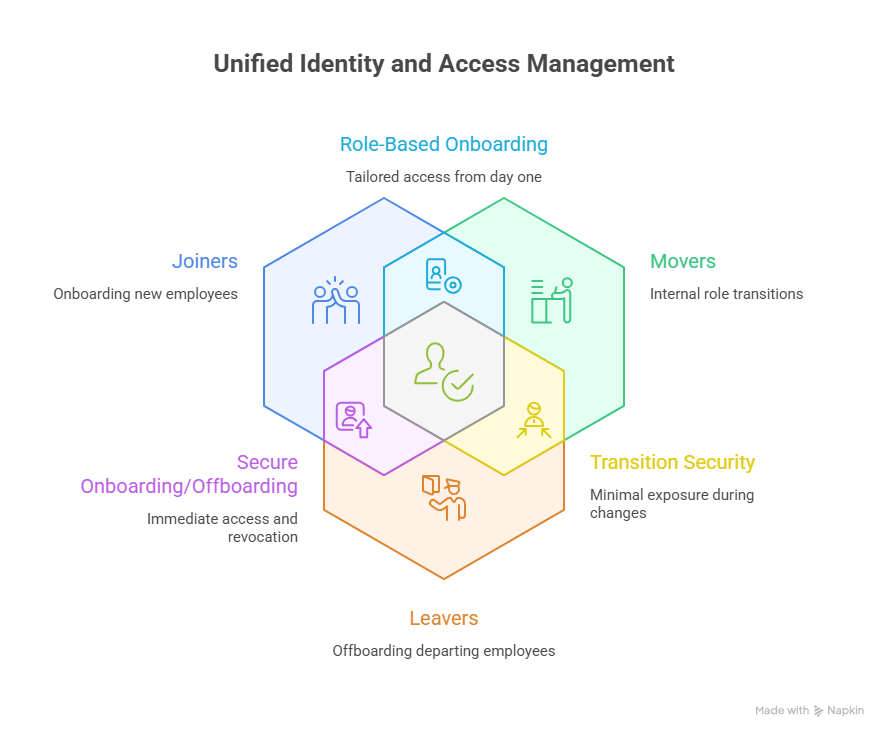
The JML framework focuses on managing access provisioning events that directly impact the protection of systems, applications, and sensitive data. The JML process governs how employee identities and permissions are handled from onboarding to offboarding:
Joiners (New Employees)
- Create user accounts and assign role-based access rights
- Provide access to required systems, applications, and data
- Enable a smooth and efficient onboarding experience while reducing manual effort and errors
Movers (Role or Responsibility Changes)
- Adjust permissions to reflect new job functions
- Remove access no longer required from previous roles
- Maintain least-privilege principles and reduce exposure during internal transitions
Leavers (Departing Employees)
- Immediately deactivate accounts and revoke all access rights
- Reclaim corporate assets such as devices and licenses
- Eliminate orphaned accounts and meet audit and compliance requirements
How to Automate the JML Process
Automating the JML process is essential for organizations seeking scalability, consistency, and stronger security controls. By integrating identity governance and administration (IGA) solutions with authoritative sources such as HR systems, access changes can be triggered automatically based on lifecycle events. Automation reduces reliance on manual processes, accelerates onboarding and offboarding, enforces standardized access policies, and provides clear audit trails. As a result, organizations can significantly lower the risk of human error, prevent unauthorized access, and ensure that Identity and Access Management keeps pace with the dynamic nature of today’s workforce.
Why does improper JML permission management pose a serious security risk?
Failing to properly manage access throughout the JML lifecycle can create significant security and compliance risks. Over-provisioned joiners may gain unnecessary access, increasing the attack surface from day one. Inadequately managed movers often retain legacy permissions, leading to privilege creep and violations of least-privilege principles. Delays or gaps in offboarding leavers can leave active accounts behind, providing attackers or former employees with unauthorized entry points into critical systems. All these issues can result in data breaches, insider threats, audit findings, and regulatory penalties. Without a disciplined and automated JML approach, organizations risk losing visibility and control over who has access to what – and why.
How to Implement a Successful JML Process?
Creating a reliable JML process requires a well-balanced approach that combines the right technologies with clearly defined governance structures. Organizations should prioritize the automation of routine identity tasks – such as account creation and access provisioning. Equally important is the establishment of well-documented policies and procedures that govern how access is granted, modified, and revoked.
Ongoing monitoring, regular access reviews, and comprehensive compliance reporting are critical to maintaining the effectiveness of the JML process. Through periodic audits, organizations can detect inconsistencies, eliminate excessive or outdated permissions, and confirm that user access remains aligned with current roles and responsibilities.
Make JML a Foundation of Your Security Strategy
Identity is a critical part of your security. Every app, device, and user action depends on proper access, making the Joiner-Mover-Leaver process a cornerstone of any effective security program. By managing identities and access throughout the employee lifecycle, organizations can enforce least-privilege principles, reduce the risk of unauthorized access, and maintain compliance with internal and regulatory requirements.
Automating JML not only ensures consistency and efficiency but also strengthens your overall security framework, providing visibility and control over who has access to what, when, and why. To achieve this in practice, PATECCO offers solutions that help organizations manage access safely and efficiently. From onboarding and role changes to offboarding and compliance documentation, PATECCO ensures every identity transition is smooth, secure, and reliable.
