Nowadays digital environments become more interconnected and Privileged Access Management (PAM) has emerged as a vital element of a strong cybersecurity defense. As digital infrastructures grow in complexity, the challenge of managing privileged accounts becomes increasingly multifaceted. A holistic PAM concept goes beyond simple password vaulting or credential rotation; it encompasses a broad, integrated approach that aligns with modern security and compliance demands.
In this article PATECCO presents an-depth look into the six key parameters essential for building a comprehensive PAM strategy:
1.Comprehensive visibility and discovery
A successful PAM strategy begins with total visibility of your privileged accounts and access points. In most organizations, privileged accounts are spread across multiple environments, including on-premises systems, cloud platforms, SaaS applications, and hybrid workloads.
Relying on manual inventory methods is no longer feasible. Instead, organizations should leverage automated discovery tools that can scan networks, endpoints, and cloud resources to identify all privileged accounts – including those that may have been forgotten or created outside standard procedures (often called “shadow admin accounts”).
Comprehensive visibility also involves continuously updating this inventory to reflect changes in the environment, such as new servers, applications, or organizational units. Only by knowing who has privileged access and where can you implement effective controls.
2. Access Governance and Least Privilege
Once visibility is achieved, the next step is implementing access governance grounded in the principle of least privilege. This principle dictates that users should have only the minimum level of access rights necessary to perform their job functions – nothing more.
Enforcing least privilege involves:
- Role-based access controls (RBAC) to assign permissions based on job responsibilities.
- Separation of duties (SoD) to prevent conflicts of interest and reduce fraud risk.
- Periodic access reviews and certifications to ensure privileges remain aligned with current roles and responsibilities.
Effective access governance not only minimizes the attack surface but also ensures regulatory compliance with standards like PCI DSS, GDPR, and HIPAA, which mandate strict controls on sensitive data.
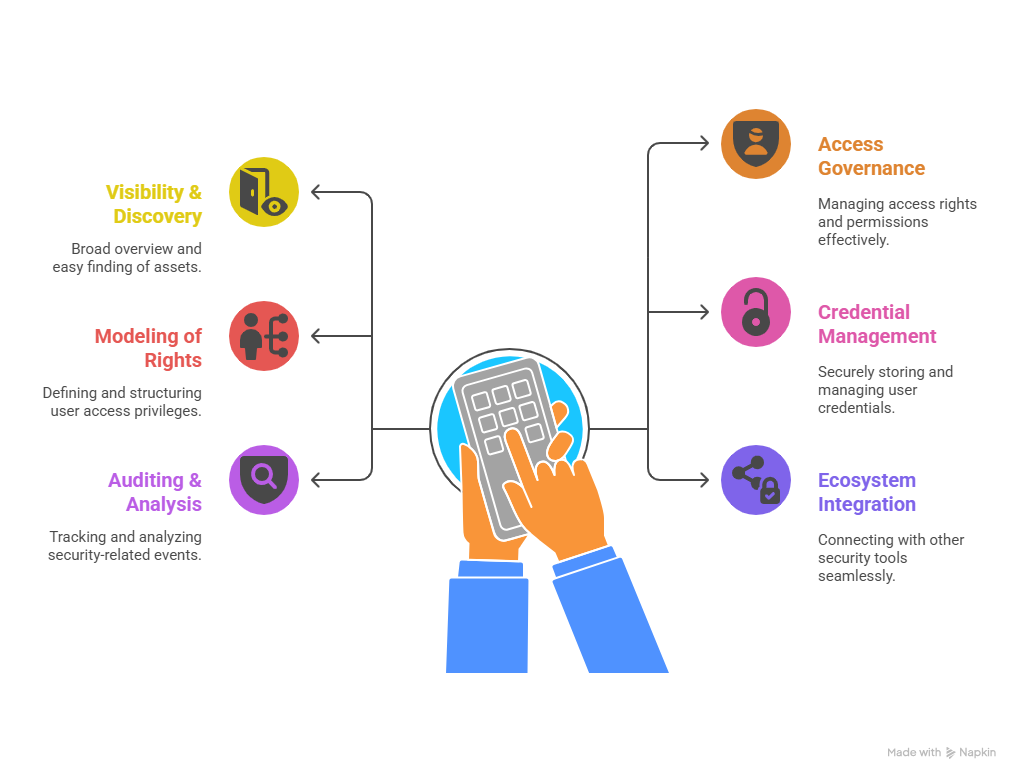
3. Modeling of Rights
A crucial component of holistic PAM is the modeling of rights – establishing a structured framework for how privileged access rights are assigned, managed, and monitored. This involves:
- Defining access models that capture typical user roles, responsibilities, and access needs within your organization.
- Mapping entitlements to these models to avoid over-provisioning.
- Dynamic access adjustments to ensure that as roles change (due to promotions, transfers, or terminations), privileges adapt accordingly.
Modeling of rights also considers the context in which access is granted, such as time of day, location, device, and other risk factors. This dynamic modeling can be implemented using risk-based or attribute-based access controls, ensuring that privileged access is adaptive and context-aware rather than static. By carefully modeling rights, organizations can prevent privilege creep and ensure that access policies evolve in line with business and security needs.
4. Credential and session management
Privileged credentials are a prime target for attackers because they offer high-level access to critical systems. A holistic PAM solution addresses this by:
- Storing credentials in secure vaults protected by encryption and multi-factor authentication.
- Automating credential rotation to eliminate static passwords, reducing the risk of credential theft.
- Eliminating embedded credentials in scripts and applications through secure APIs or ephemeral tokens.
Equally important is session management. By recording privileged sessions – whether through video or keystroke logs – organizations gain a comprehensive audit trail of all privileged activities. Session monitoring also enables real-time termination of suspicious behavior, limiting potential damage from insider threats or external breaches.
5. Auditing, monitoring and analytics
Security is not a “set and forget” process. A robust PAM program includes continuous auditing and monitoring of privileged activities. Key elements include:
- Detailed activity logs to track who accessed what and when.
- Real-time alerts for policy violations, suspicious behavior, or failed login attempts.
- Behavioral analytics and machine learning to identify anomalies that may indicate compromised credentials or insider misuse.
These insights not only bolster security but also support regulatory compliance. Regulators increasingly require organizations to demonstrate robust auditing capabilities and the ability to investigate security incidents quickly and thoroughly.
6. Integration with broader security ecosystem
Finally, a holistic PAM concept must not exist in isolation. It should integrate seamlessly with the broader security and IT ecosystem, including:
- Identity and Access Management (IAM) platforms to unify identity governance across all users, not just privileged accounts.
- SIEM (Security Information and Event Management) solutions to correlate privileged activity with other security events for a comprehensive threat picture.
- Endpoint detection and response (EDR) tools to extend privileged access protection to endpoints and workstations.
Such integration enables organizations to leverage existing security investments and create a unified, adaptive defense posture that can respond swiftly to emerging threats.
Privileged access remains one of the most critical and vulnerable components of any IT infrastructure. By addressing these six parameters, organizations can move beyond fragmented, reactive approaches to PAM and instead embrace a holistic, proactive security framework that adapts to evolving risks and compliance mandates. Building and maintaining a holistic PAM strategy is an ongoing journey. It requires constant vigilance, continuous improvement, and a commitment to aligning security with business needs.
If you’d like to assess your current PAM maturity or explore solutions to implement these principles effectively, feel free to connect with us: info@patecco.com; +49 (0) 23 23 – 9 87 97 96 . Securing privileged access isn’t just about technology – it’s about safeguarding your organization’s most valuable assets.
