Identity Fabric is quickly becoming the strategic pillar of modern Identity and Access Management. However, many organizations still face challenges in aligning their IAM strategies with the changing market demands. To be effective, Identity Fabric must unify core IAM functions such as Identity Governance and Administration (IGA), Access Management (AM), Privileged Access Management (PAM), and more. This convergence not only strengthens identity management but also enables organizations to meet emerging requirements like Zero Trust architecture, decentralized identities, and dynamic, policy-based access control.
How Identity Fabric Helps Protect User Identity
In the complex digital infrastructures, protecting user identities requires a holistic, integrated approach. An identity fabric is a framework for integrating and orchestrating multiple identity and access management (IAM) systems to act as a single unified system. The identity fabric gives organizations a centralized approach to securing and managing digital identities in complex IT environments. This centralized approach improves visibility into user activity, strengthens the organization’s security status and operational efficiency and supports a more streamlined user experience.
An identity fabric helps unify disconnected identity systems across an organization’s digital ecosystem. This unification makes it easier to monitor activity and apply consistent identity governance, authentication and authorization measures for all users across every application and platform.
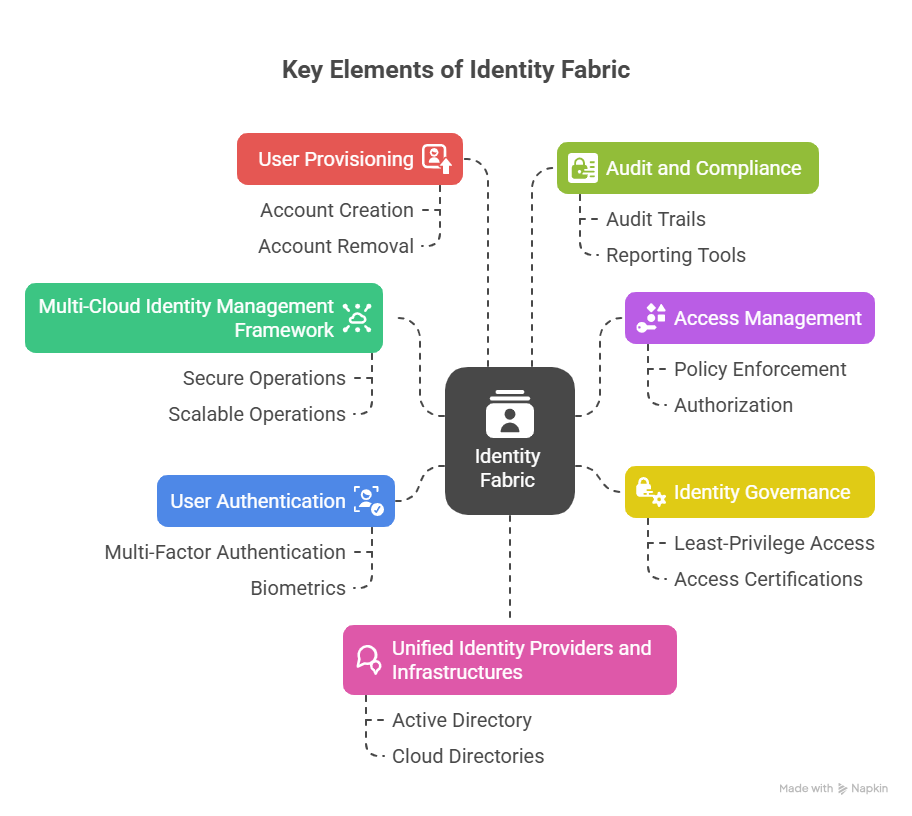
Key Elements of Identity Fabric:
1. Multi-Cloud Identity Management Framework
Serves as a foundation for managing identities consistently across cloud platforms, enabling secure and scalable identity operations in multi-cloud and hybrid environments.
2. Access Management
Controls who can access which resources, enforcing policies that govern user permissions and ensuring that only authorized individuals can reach sensitive data or systems.
3. User Authentication
Verifies user identities using methods such as multi-factor authentication (MFA), biometrics, or adaptive authentication to prevent unauthorized access.
4. User Provisioning
Automates the creation, updating, and removal of user accounts and access rights across systems, ensuring users have the correct level of access throughout their lifecycle.
5. Audit and Compliance
Tracks identity-related activities and changes, providing audit trails and reporting tools that support regulatory compliance and security monitoring.
6. Unified Identity Providers and Infrastructures
Integrates multiple identity sources (such as Active Directory, cloud directories) into a single, cohesive identity layer to streamline authentication and authorization processes.
7. Identity Governance
Manages risk and compliance by enforcing least-privilege access, conducting periodic access certifications, entitlement reviews, and separation-of-duties checks to ensure permissions remain appropriate over time.
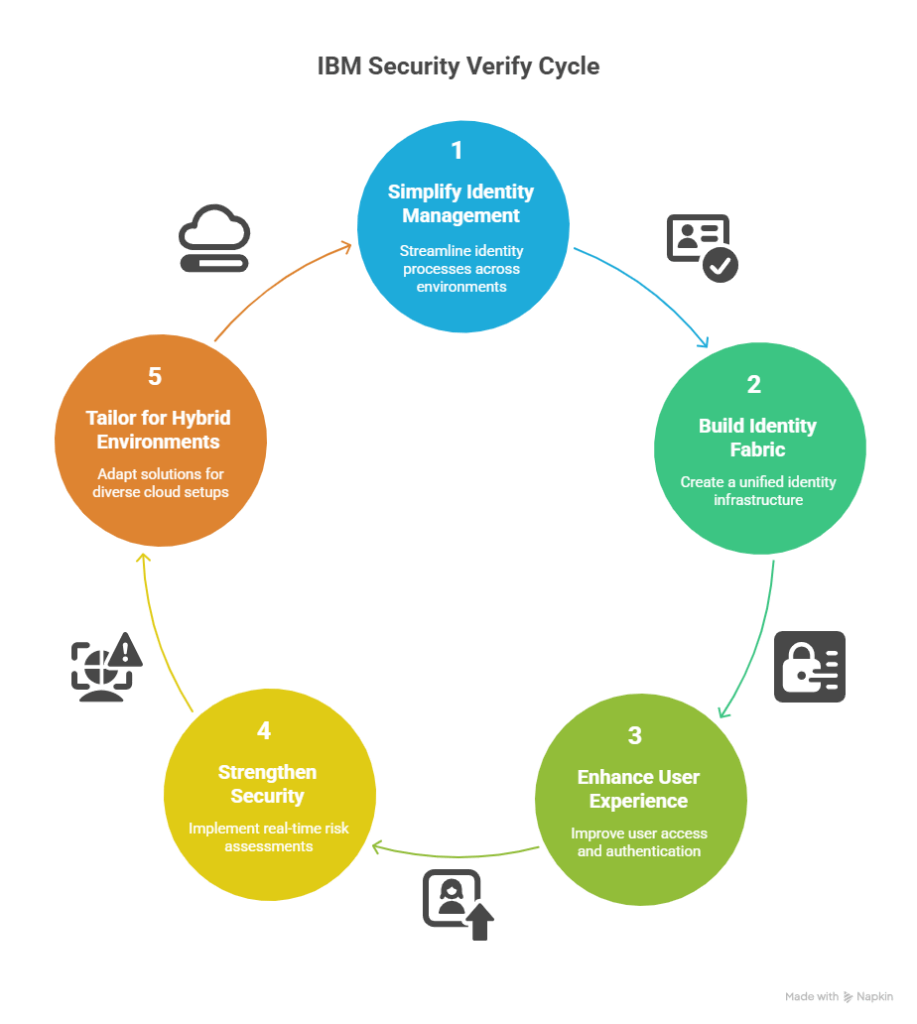
IBM Security Verify – Simplifying Identity Management Across Multi-Cloud and Hybrid Environments
First, let’s clarify – what is IBM Security Verify? This is a suite of identity solutions that simplify identity management across hybrid environments and build an identity fabric with vendor-neutral tools.
IBM Security Verify suite offers the essential components needed to build an identity fabric, that help organizations address identity challenges arising from cloud migration and digital transformation. It eliminates identity silos and enhances user experience by applying modern authentication methods to legacy applications without requiring code changes, ensuring a seamless and consistent experience across all applications. Additionally, it strengthens security through real-time behavioral and biometric risk assessments.
The IBM Security Verify suite delivers advanced identity and access management tailored for hybrid and multi-cloud environments. It supports automated, cloud-based, and on-premises identity governance, workforce and consumer identity management, and privileged access control. Together, IBM’s Identity Fabric and Security Verify solutions unify complex identity infrastructures, boost security, enhance user experience, and provide scalable identity management capabilities.
Why implementing Identity Fabric is important for your business?
Adopting an Identity Fabric architecture offers organizations a modern, adaptive approach to securing digital identities across increasingly complex IT environments. Unlike traditional IAM systems, which often operate in silos, Identity Fabric delivers a unified and flexible framework that scales with business needs while maintaining robust security controls.
Key benefits include:
- Comprehensive Visibility and Control
Gain centralized oversight of all user identities and access points, enabling real-time monitoring, risk analysis, and policy enforcement across cloud, on-premises, and hybrid systems. - Improved Security Resilience
By integrating identity governance, authentication, access management, and privileged access control, Identity Fabric reduces attack surfaces and strengthens defense against threats like identity theft, account compromise, and insider risk. - Seamless User Experience
Provide users with secure, frictionless access through features like single sign-on (SSO), adaptive authentication, and federated identity, without compromising security. - Operational Efficiency and Automation
Streamline identity processes such as user provisioning, deprovisioning, and policy management, reducing manual workload and minimizing errors. - Support for Zero Trust and Modern Architectures
Identity Fabric supports strategic security initiatives such as Zero Trust, decentralized identity models, and policy-based access, enabling organizations to meet the regulatory and operational requirements. - Long-Term Scalability
Easily extend IAM capabilities to new applications, cloud platforms, or identity providers as your organization grows, without rearchitecting the entire system.
By implementing an Identity Fabric, organizations can not only protect identities more effectively but also enable secure digital transformation.IBM Security Verify plays a key role in this approach, offering the essential tools to build a scalable and robust identity fabric. With its modern capabilities – from risk-based authentication to identity governance – it helps organizations simplify identity management while adapting to the changing business and security demands.
Sources:
