In a world defined by remote work, digital processes, cloud adoption and increasing cyber threats, businesses must ensure that users can access the right systems efficiently, but also that this access remains appropriate and secure. This balance is achieved through two interconnected but distinct practices – Identity Management and Identity Governance.
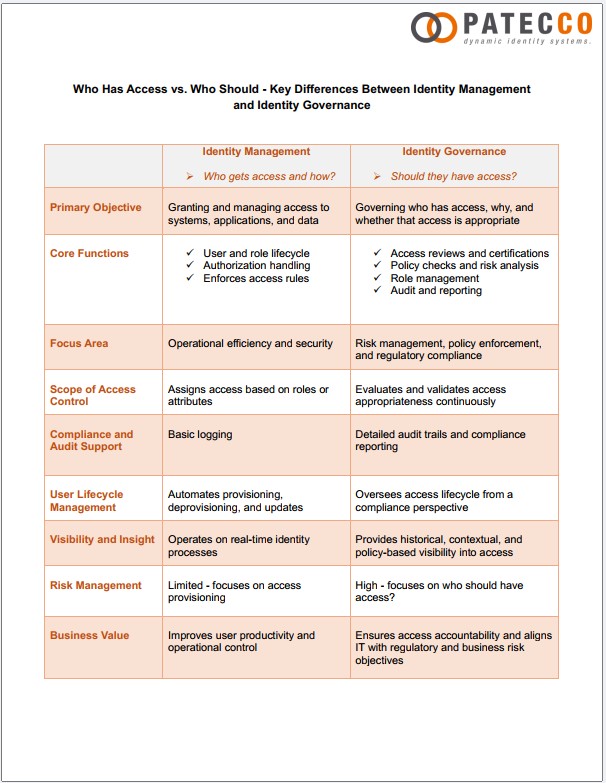
While these concepts are often implemented together as part of a broader identity and access management strategy, they serve very different purposes. Identity Management is concerned with how users get access, whereas Identity Governance focuses on whether users should have that access. Understanding the key differences between the two is essential for organizations aiming to strengthen their security posture and meet compliance obligations.
Identity Management – Who gets access and how?
Identity Management refers to the processes and technologies that handle the creation, maintenance, and removal of user identities and their access permissions across systems, applications, and data sources. Its main goal is to streamline how access is granted – ensuring that users can quickly and efficiently begin working with the tools they need.
Identity Management solutions are designed for operational efficiency. They typically assign access based on roles or attributes (such as department or job function) and automate tasks like provisioning new accounts, updating access when roles change, and deprovisioning users when they leave the organization.
While this automation increases productivity and reduces administrative burden, Identity Management systems often provide only basic logging capabilities. They do not typically validate whether access is still necessary or aligned with business policies.
Identity Governance – Should they have access?
Identity Governance, in contrast, adds oversight and accountability to the access process. Rather than focusing on how access is granted, Identity Governance asks: Should the user have access?
Identity Governance provides capabilities that include: Regular access reviews and certifications, policy checks and risk analysis, role management, audit and reporting.
Where Identity Management ensures that access is delivered efficiently, Identity Governance ensures that access is monitored, reviewed, and justified. It supports risk management by identifying excessive or unnecessary permissions and helps enforce business rules like segregation of duties. Moreover, Identity Governance offers historical and contextual visibility into access decisions, allowing organizations to answer critical questions during audits or incidents: Who had access to what, when, and why?
Different focus, but shared goal
Though closely related, Identity Management and Identity Governance differ significantly in their areas of focus:
- Identity Management emphasizes operational efficiency and security by automating identity-related tasks and enforcing access rules in real-time.
- Identity Governance emphasizes risk management, compliance, and policy enforcement, ensuring access remains appropriate over time and meets both regulatory and organizational standards.
Both play vital roles across the user lifecycle. While Identity Management automates the initial granting of access, Identity Governance oversees the lifecycle from a compliance and business risk perspective.
Why Organizations Need Both
Implementing only Identity Management without Identity Governance can result in users accumulating access they no longer need – also known as „access creep“ – which increases risk. On the other hand, relying solely on Identity Governance without the automation provided by Identity Management leads to inefficiencies and delays.
To properly protect sensitive data, support compliance, and enable business agility, organizations must adopt both. Identity Management ensures access is provided efficiently, while Identity Governance ensures that access remains appropriate and accountable.
The difference between Identity Management and Identity Governance is not just a technical distinction. By integrating both practices, organizations can not only enhance operational control but also ensure they meet today’s strict security and regulatory standards – without compromising user productivity. Together, they create a secure, compliant, and well-managed digital environment.
Download PATECCO’s free one-pager: Identity Management vs. Identity Governance.