In a technology-dominated world, no organization is immune to cyber threats. Even companies that consider themselves “secure” can harbor hidden vulnerabilities that expose them to data breaches, system downtime, and financial loss. Identifying these weaknesses before they become critical issues is essential.
This is where a GAP analysis comes in. Often used in IT security, a GAP analysis provides a structured approach to evaluate your current security measures against best practices, regulatory requirements, and potential threats. By highlighting areas where your defenses are weak, it enables you to take proactive steps to strengthen your IT infrastructure.
In this blog post, we explore what a GAP analysis is, why it’s crucial for modern businesses, and how you can use it to uncover and close security gaps. Whether you’re an IT professional, a business owner, or simply interested in cybersecurity, this guide will equip you with practical insights to safeguard your organization against potential risks.
What is a GAP analysis:
- Process of analyzing where a company is, where it should be, the differences between the two and determining how to implement change.
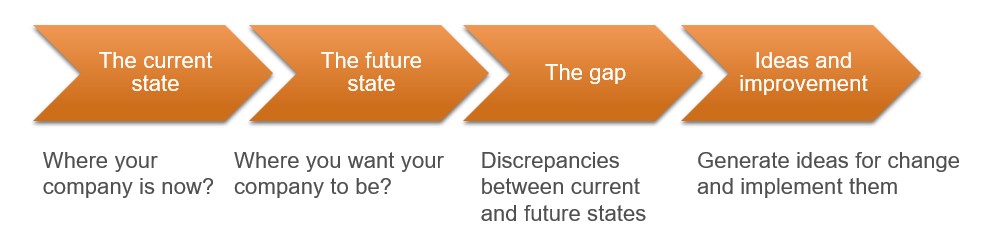
- The four gap analysis stages are called the current state, the future state, the gap, and ideas and improvement.
- In IT security, this means checking your current protections against best practices or standards.
- The aim is to find weaknesses and create a clear plan to fix them.
GAP Analysis Process:
- Identify: Clarify objectives, goals, and desired outcomes thoroughly
- Investigate: Examination of disparities between current and desired conditions thoroughly.
- Decide: Choose strategies to bridge identified gaps effectively and efficiently.
- Implement: Execute strategies with clear actions, responsibilities, and timelines.
- Analysis: Evaluation of disparities between current and desired states concisely.
- Improve: Enhance efficiency, accuracy, and effectiveness of gap analysis methods.
When should you conduct a GAP Analysis?
- Usually performed at the start of ISO certification or when implementing security standards.
- Can be repeated anytime to ensure ongoing compliance and effectiveness.
- Ideal for regular IT security health checks to catch new risks early.
- Valuable during system updates, upgrades, or when integrating
- new technologies.
- Provides a valuable view from outside without operational blindness.
Common challenges and how to overcome them?
- Inaccurate or outdated security policies: Overcome by regularly reviewing and updating policies to reflect current threats and technologies.
- Lack of expertise in security frameworks: Overcome by involving external consultants or training internal staff on relevant standards.
- Limited budget for security improvements: Overcome by prioritizing gaps based on risk and potential impact, focusing on high-risk areas first.
- Difficulty measuring security improvements: Overcome by defining clear metrics like Key Performance Indicators or Critical Success Factors and regularly reviewing progress against them.
Why is GAP Analysis important for your business?
- Helps identify weaknesses and vulnerabilities before they cause problems.
- Provides a clear picture of where your IT security stands versus best practices.
- Guides focused improvements by highlighting the most critical gaps.
- Supports compliance with industry standards and regulations.
- Reduces risks by proactively addressing potential security flaws.
- Drives continuous improvement in your security resilience over time.
Download PATECCO’s practical guide here:

