As digital technologies continue to transform how organizations operate, securing network infrastructure has become a top priority. Traditional security measures, such as firewalls, intrusion detection systems, and antivirus software, have proven effective in defending against a variety of cyber threats. However, the increasing sophistication of cyberattacks has exposed the limitations of these conventional systems. This is where User Behavior Analytics (UBA) emerges as a powerful tool in the defense against modern network security threats. By focusing on the patterns and behaviors of individual users, UBA can detect anomalies and malicious activities that traditional security tools might overlook.
What is User Behavior Analytics (UBA)?
User Behavior Analytics is a cybersecurity technology that uses machine learning, statistical analysis, and data mining techniques to monitor and analyze user activities within a network. UBA systems are designed to create baseline profiles of normal user behavior, which can then be compared to real-time activities to identify deviations. These deviations – often indicative of potential security threats – are flagged for further investigation by security teams.
UBA tools collect and analyze various data points, such as login times, IP addresses, file access patterns, application usage, and device behavior. The goal is to gain insight into user activity across a network, identify any unusual behavior, and trigger alerts when a potential security incident is detected. This form of behavior-centric analysis allows organizations to proactively identify insider threats, detect compromised accounts, and mitigate the impact of external cyberattacks.
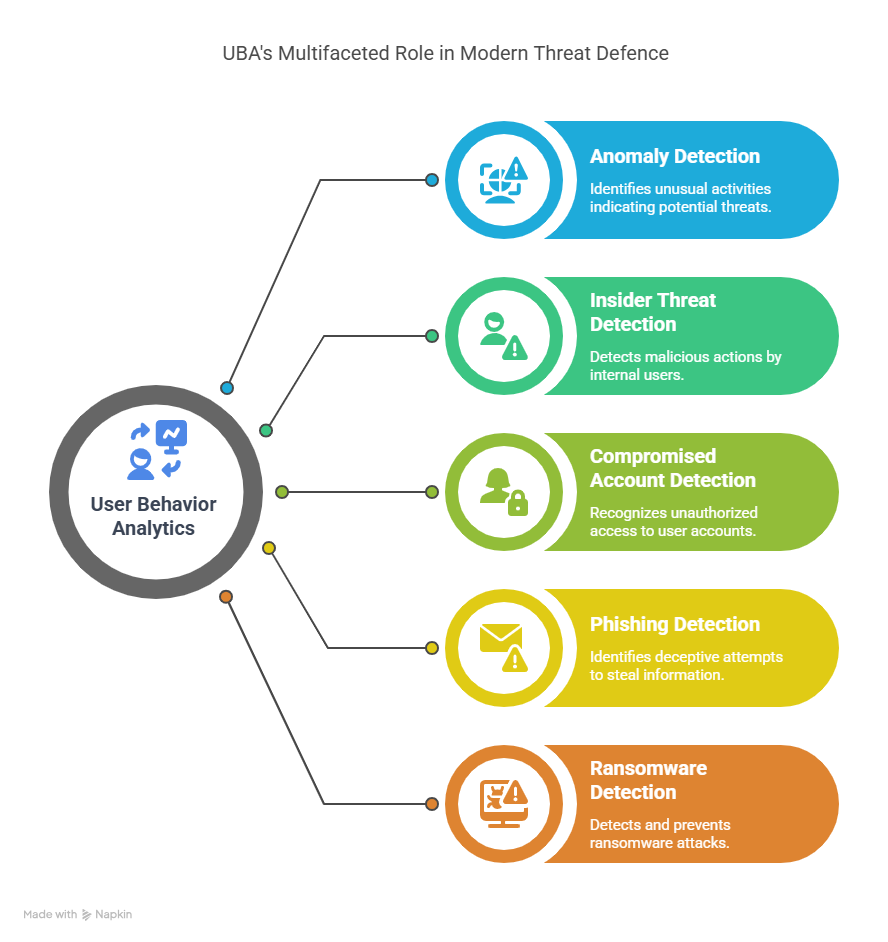
How does user Behavior Analytics detect network security threats?
UBA detects network security threats in five key ways:
1. Anomaly detection
One of the primary ways UBA detects security threats is through anomaly detection. By continuously monitoring user activity and comparing it against a predefined baseline of normal behavior, UBA systems can identify when a user or group of users deviates from their typical patterns. Common anomalies that may indicate a security threat include:
- Login from an unusual location: If a user logs into the network from an IP address or geographic location that is inconsistent with their usual activity, it could be a sign of a compromised account or a brute force attack.
- Unusual working hours: A user accessing the network at odd hours outside of their normal work schedule may signal malicious behavior or an insider threat.
- File and data access anomalies: Excessive or unusual access to sensitive files, especially if a user is accessing files they don’t normally interact with, could point to data exfiltration or an attempt to steal intellectual property.
2. Detecting insider threats
Insider threats, whether from disgruntled employees or compromised accounts, are one of the most difficult types of security threat to detect. UBA tools are particularly effective in identifying these threats by monitoring employee behavior for any signs of suspicious activity. If a trusted user suddenly begins to access sensitive information without authorization, or exhibits other signs of suspicious behavior, UBA systems can raise alerts. These threats can be further investigated to determine whether the user’s actions are a result of malicious intent or a compromised account.
3. Compromised account detection
A compromised account is one of the most common methods used in cyberattacks. Hackers often use stolen credentials to access sensitive networks and systems. UBA can detect a compromised account through unusual patterns, such as:
- Login attempts from unfamiliar devices: If a legitimate user’s credentials are used to log in from an unfamiliar device or location, UBA systems can flag this behavior.
- Escalation of privileges: If a user suddenly gains access to high-level administrative rights that they previously did not have, it could indicate that the account has been compromised.
- Unusual behavior patterns: If a user begins to download or transfer large volumes of data that are inconsistent with their normal activities, UBA can identify this behavior as a potential data breach.
4. Phishing detection
Phishing attacks are one of the most common and successful forms of cyberattack. UBA can help detect phishing attacks in the early stages by monitoring email interactions and identifying patterns associated with phishing attempts. For example, if a user begins responding to unusual emails or accessing links from suspicious sources, UBA systems can trigger an alert for further investigation.
5. Ransomware detection
Ransomware attacks typically begin with a user unknowingly downloading malicious software that encrypts files and demands payment for the decryption key. UBA can identify the early stages of a ransomware attack by detecting unusual file access patterns or the sudden modification of files that a user would not typically engage with. By identifying these behaviors early on, UBA systems can help prevent ransomware from spreading throughout the network.
How UBA Defends Against Network Security Threats
While detecting threats is critical, the defensive capabilities of User Behavior Analytics go a step further in actively protecting the network. UBA can integrate with other security systems, such as Security Information and Event Management (SIEM) platforms to enable a coordinated defense strategy.
1. Real-time alerts and response
Once a suspicious behavior is detected, UBA systems can generate real-time alerts to notify security teams. These alerts can be prioritized based on the severity of the detected threat. Security analysts can then investigate the alert, isolate the affected systems, and initiate incident response protocols to mitigate the impact of the attack.
2. Automated responses
Many UBA solutions integrate automated response mechanisms, which can take immediate action to contain potential threats. For example, if a user’s account shows signs of compromise, the system can automatically lock the account or initiate multi-factor authentication to confirm the user’s identity before granting access. Automated responses help to reduce the time to detection and prevent threats from escalating.
3. Mitigation of false positives
UBA systems use machine learning to improve their detection accuracy over time. As the system continues to monitor user behavior, it becomes better at distinguishing between normal and abnormal activity. This helps to reduce the number of false positives, ensuring that security teams focus on genuine threats rather than wasting time on benign activities.
4. Risk-based approach
By continuously analyzing user behavior, UBA helps security teams prioritize threats based on the level of risk they pose to the organization. For example, if a high-ranking executive’s account is exhibiting suspicious behavior, it may warrant a higher priority investigation than a low-level employee. This risk-based approach ensures that resources are allocated efficiently and that the most critical threats are addressed first.
Key Takeaways
User Behavior Analytics has emerged as a critical tool in the fight against modern network security threats. By leveraging advanced machine learning, data analysis, and anomaly detection techniques, UBA provides organizations with the ability to monitor and analyze user behavior in real-time. This enables the early detection of insider threats, compromised accounts, and other security risks that traditional methods may miss.
As cyber threats continue to evolve, UBA will play an increasingly important role in defending against attacks. By providing a more proactive, behavior-focused approach to network security, organizations can better protect their networks, sensitive data, and critical assets. The combination of advanced analytics and automated responses makes UBA an indispensable part of any comprehensive cybersecurity strategy.
Whether you have questions about cybersecurity, need advice on IAM solutions, or want to explore a potential collaboration, feel free to reach out at info@patecco.com or call +49 (0) 23 23 – 9 87 97 96 .
