With the growing amount of sensitive data being stored and accessed across various platforms, ensuring strong data protection has become a top priority for organizations of all sizes. One effective solution to mitigate these risks is Role-Based Access Control (RBAC). This security model enables organizations to limit access to data based on an individual’s role within the organization. In this article, we’ll highlight how RBAC can be used to reduce data leakage and data breaches by ensuring that access to sensitive information is strictly controlled, minimizing the risk of unauthorized access, and helping organizations maintain compliance with security standards.
The risks of data leakage and data breaches
Data leakage and data breaches pose significant risks to organizations, both financially and reputationally. Data leakage, whether accidental or unintentional, can expose sensitive information to unauthorized individuals, often resulting in compliance violations, legal consequences, and loss of trust. On the other hand, data breaches, which typically involve malicious actors gaining unauthorized access, can lead to the theft of valuable personal or corporate data, such as financial details or intellectual property.
Both incidents can cause severe damage to a company’s reputation, erode customer confidence, and result in costly fines, especially when regulatory compliance requirements are not met. In an increasingly interconnected world, the risks associated with these breaches are more prominent, making it crucial for organizations to adopt robust data protection measures.
Key principle of Role-Based Access Control (RBAC)
The key principle behind RBAC is the principle of least privilege: users are only granted the minimum level of access required to perform their job functions. By assigning access permissions based on roles rather than individuals, RBAC ensures that users are given the minimum level of access required, reducing the risk of accidental or intentional misuse of sensitive data. This principle not only helps in enhancing security but also streamlines access management, ensuring that only authorized individuals can interact with critical information.
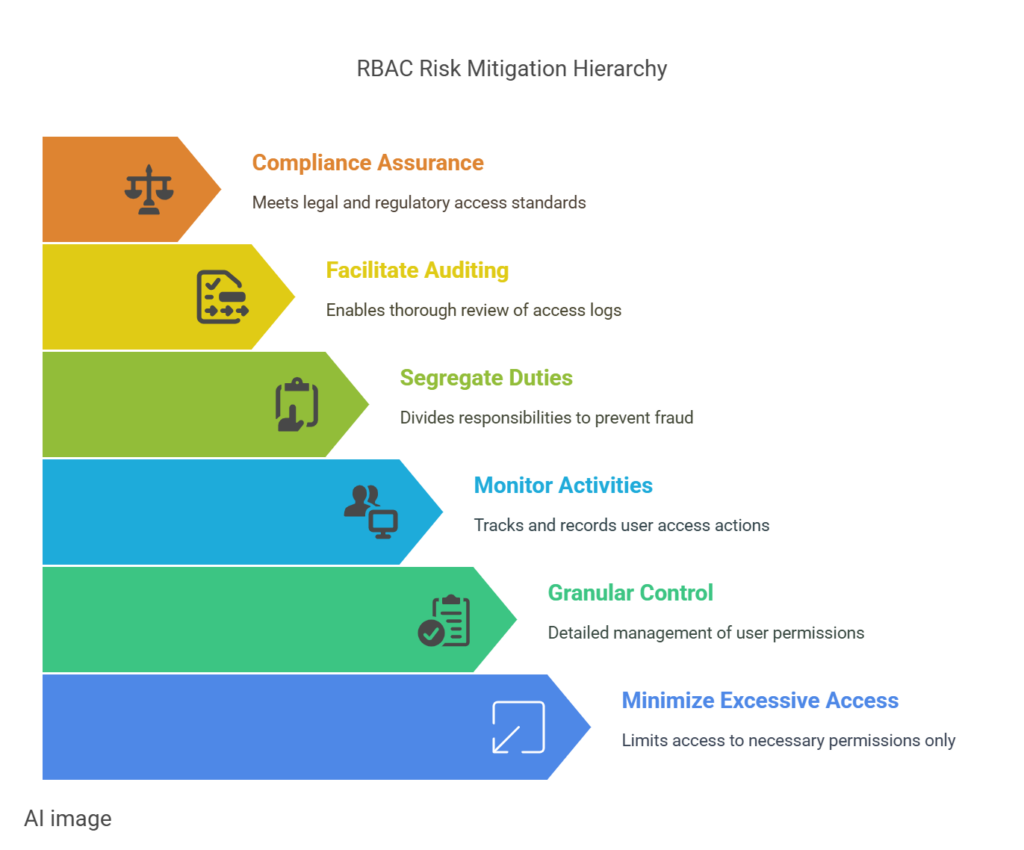
How RBAC Reduces Data Leakage and Data Breaches
- Minimizing excessive access: One of the primary causes of data leakage and breaches is the over-provisioning of access. When employees have access to more data than necessary, the risk of exposure—whether accidental or intentional—rises. RBAC helps address this by ensuring that users only have access to the data that is relevant to their role. By restricting access to sensitive information, the likelihood of accidental or malicious data leakage decreases.
- Granular control over permissions: RBAC enables administrators to define roles with very specific permissions. For example, a “manager” might have access to read and write data, while an “analyst” might only have read access. This level of granularity ensures that employees can only perform actions that are essential for their job functions, significantly reducing the possibility of data breaches.
- Monitor and log access activities: One of the key advantages of implementing Role-Based Access Control (RBAC) is the ability to monitor and log user access activities in a detailed and structured manner. By tracking who accessed what data and when, organizations can gain valuable insights into potential security threats or unauthorized behavior. For instance, if a user suddenly accesses data they do not typically interact with, this can trigger an alert for further investigation. Regularly reviewing these logs helps organizations spot vulnerabilities, enforce security policies, and respond quickly to potential breaches.
- Segregation of Duties: By clearly defining roles and responsibilities, RBAC ensures segregation of duties – this is a concept where critical tasks are split across different roles to prevent any single individual from having too much power. This reduces the likelihood of malicious insiders exploiting their position to access sensitive data without oversight. For example, one person may have access to request data, while another has the ability to approve its release.
- Auditing and monitoring: RBAC typically integrates with logging and monitoring tools, making it easier to track who accessed what data and when. This enables organizations to detect unauthorized access attempts, monitor for suspicious activities, and investigate any incidents that do occur. If a data breach does happen, having a clear audit trail can help identify the source of the breach and mitigate further damage.
- Compliance with regulations: Many regulatory frameworks, such as GDPR, HIPAA, and PCI-DSS, require organizations to implement strict data access controls. RBAC helps businesses comply with these regulations by ensuring that only authorized personnel can access sensitive data. It also simplifies the process of reporting and auditing access, which is a key requirement for many compliance standards.
As mentioned, data leakage and data breaches pose serious risks to organizations, but by implementing Role-Based Access Control (RBAC), businesses can significantly reduce their vulnerability. When combined with other security measures, such as multi-factor authentication and employee education, RBAC forms a comprehensive strategy to safeguard critical information and maintain compliance with regulations.
RBAC is not a one-size-fits-all solution, but when implemented correctly, it is an essential part of a broader data security strategy. By taking the time to define roles, assign appropriate permissions, and continually monitor access, organizations can protect their data from leakage, breaches, and other security threats in the ever-evolving digital landscape.
Interested in getting advice from PATECCO‘s expert? Book Your Free 30-Minute Consultation!

