Nowadays, organizations face increasing pressure to secure critical systems, sensitive data, and user access. While Identity and Access Management (IAM) governs broad organizational access, Privileged Access Management (PAM) focuses on accounts with elevated privileges that can significantly impact business-critical systems. Individually, IAM and PAM provide essential layers of security, but when integrated effectively, they create a synergistic framework that enhances security, simplifies compliance, and strengthens operational resilience.
Integration and Compatibility
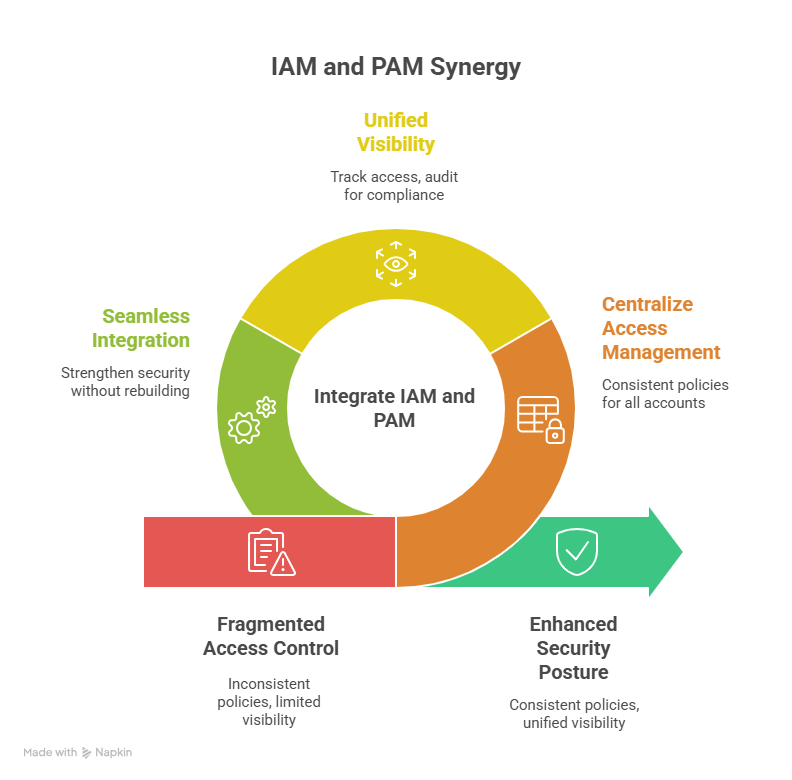
Integrating IAM and PAM allows organizations to unify access control policies and ensure consistent oversight across all users. IAM handles authentication, role-based access, and user lifecycle management, ensuring employees, contractors, and partners have appropriate access to resources. PAM complements IAM by securing privileged accounts, providing controls for sensitive operations, and monitoring high-risk activities.
This integration delivers tangible benefits:
- Centralized access management ensures that policies are applied consistently to both regular and privileged accounts.
- Unified visibility enables security teams to track who is accessing what, when, and how – audit trails also provide critical insights for compliance.
Modern PAM solutions are increasingly designed to integrate seamlessly with existing IAM frameworks, directories, and identity providers. This allows companies to strengthen their security architecture without having to completely rebuild their infrastructure.
Integration Challenges
While the benefits of uniting IAM and PAM are significant, the process also presents critical challenges. Understanding these hurdles early allows organizations to plan effectively and reduce risks during implementation. The most common challenges include:
- Legacy systems and siloed applications
Many organizations still rely on outdated infrastructure or isolated systems that were not designed to integrate easily. These environments often require custom connectors, which add complexity, time, and cost to the deployment process.
- User resistance and cultural barriers
Administrators and employees may resist new security protocols, especially if they perceive them as adding extra steps or slowing down workflows. Overcoming this resistance requires clear communication, user training, and strong change management.
- Policy alignment between IAM and PAM
IAM policies typically cover general user access, while PAM deals with high-level privileges. Aligning these two policy frameworks can be challenging, because rules designed for standard accounts often need significant adaptation to address privileged access securely and consistently.
- Scalability of the integration
A successful IAM-PAM integration must not only meet current needs but also scale with the organization as it grows. This includes supporting new applications, cloud environments, and evolving regulatory requirements without creating performance bottlenecks. Those who recognize and address these challenges early on and work with a structured plan – for example, through a gradual introduction, clear coordination of guidelines, and the involvement of relevant stakeholders – can achieve smooth and effective integration.
Best Practices for Successful Deployment
For successful IAM and PAM integration, organizations should start with a thorough assessment of their environment. The following best practices can help organizations minimize risks and maximize the value of their deployment:
1. Conduct a comprehensive inventory of the environment
Identifying all users, applications, and privileged accounts to understand integration needs.
2. Define uniform access policies
Once the environment is mapped, defining unified access policies ensures consistent rules for regular and privileged accounts.
3. Implement phased deployment
Adopting a phased deployment approach – this minimizes disruption to business operations, allows teams to test and refine policies, and helps build confidence among stakeholders.
4. Train and involve stakeholders
Training administrators, employees, and decision-makers is critical, as adoption depends on understanding new workflows and security protocols and the value behind them.
5. Continuous monitoring and optimization
Continuous monitoring and optimization further ensure that IAM and PAM operate efficiently, with periodic reviews of access logs, compliance reports, and system performance providing insights for ongoing improvement. By following these practices, organizations can build a scalable and resilient integration strategy that not only secures their digital environment but also enables long-term growth and compliance.
How can PATECCO support you to secure and manage user identities and access rights?
At PATECCO, we help organizations leverage the synergy between IAM and PAM to build a comprehensive security strategy. We begin with expert assessment and planning, identifying each organization’s unique IAM and PAM requirements. Our team ensures seamless integration between existing IAM systems and advanced PAM solutions, maintaining operational continuity and minimizing disruption.
We also provide deployment support and ongoing optimization through continuous monitoring, policy refinement, and proactive guidance. With over 20 years of experience in IAM and PAM, PATECCO enables companies to turn unified identity and privileged access management into a competitive advantage, improving security, compliance, and operational reliability.
If your organization is looking for a trusted IAM partner to enhance your cybersecurity resilience and support scalable, long-term compliance, don’t hesitate to get in touch with us. We are here to help you turn information security into a true business advantage.

