We are living through a profound transformation in how organizations operate and secure their digital environments. Artificial Intelligence (AI) and Identity and Access Management (IAM) have moved far beyond being industry buzzwords. Together, they are becoming the driving forces behind the modern workplace. As enterprises accelerate their efforts to automate processes, increase productivity, and defend against constantly developing security threats, the convergence of AI and IAM is enabling a workplace that is not only smarter and safer, but also more adaptive and user-centric.
- AI and IAM: A New Challenge for Companies
The integration of AI into IAM is both an opportunity and a challenge. On one hand, AI can deliver unprecedented visibility, automation, and proactive risk management. On the other hand, deploying AI in sensitive identity systems requires careful governance, data privacy safeguards, and trust in the decision-making process.
Organizations must balance these considerations while adopting AI-enhanced IAM. The companies that succeed will not only secure their environments but also unlock operational efficiency and a competitive edge. However, success depends on more than just adopting advanced tools, it requires a thoughtful strategy. Clear policies, transparent algorithms, and strong human oversight are essential to ensure that AI-driven decisions remain fair, explainable, and aligned with regulatory requirements.
Integrating AI into IAM often alters established workflows, demanding closer collaboration between IT, security, compliance, and business teams. Companies that prepare their people and processes alongside their technology will be better positioned to realize the full value of AI in IAM.
- How AI Enhances IAM?
AI is transforming Identity and Access Management by moving it from static, rule-based controls to dynamic, intelligent systems that adapt in real time. It enables faster decision-making, improves security, and reduces complexity while delivering smoother user experience. The key areas where AI is making an impact include:
Automated Onboarding/Provisioning
Traditional onboarding and provisioning often involve manual intervention and rule-based workflows that are prone to delays and errors. AI streamlines this process by:
- Role-based recommendations: AI analyzes existing user roles, entitlements, and access histories to suggest the right level of access for new employees or contractors.
- Dynamic provisioning: Instead of static templates, AI adjusts access privileges in real-time based on job function, department, and historical patterns.
- Error reduction: By learning from prior provisioning outcomes, AI minimizes over-provisioning (granting excessive access) and under-provisioning (restricting critical access).
This leads to faster onboarding, reduced administrative burden, and improved compliance with least-privilege principles.
Anomaly Detection
Cyber attackers often exploit compromised credentials or misuse legitimate access. Detecting such threats requires more than simple rule-based monitoring. AI-driven anomaly detection uses machine learning models to identify deviations from normal user behavior, such as:
- Unusual login times or geographies
- Access requests inconsistent with job roles
- Abnormal data downloads or system usage
By continuously learning and adapting, AI-based anomaly detection can surface risks in near real time, enabling security teams to intervene before threats escalate.
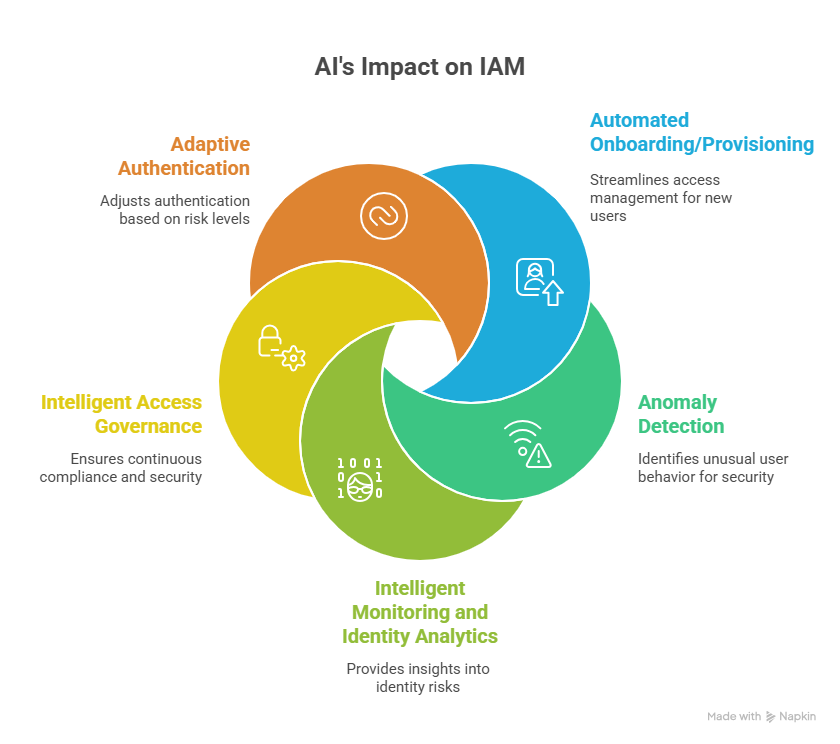
Intelligent Monitoring and Identity Analytics
Traditional IAM reporting tools often generate static dashboards and alerts that require manual interpretation. AI enhances monitoring and analytics by:
- Correlating disparate data sources: AI consolidates logs from cloud, on-premises, and third-party systems, providing a unified identity risk view.
- Behavioral baselining: By understanding “normal” activity, AI highlights subtle anomalies that may indicate insider threats or credential misuse.
- Predictive insights: Instead of only describing what happened, AI predicts potential risks – such as accounts likely to be compromised or roles prone to privilege creep.
This intelligence helps organizations move to proactive identity risk management.
Intelligent Access Governance
Access governance has traditionally relied on periodic reviews and manual audits, which are time-consuming and prone to oversight. AI brings intelligence to governance through:
- Automated access reviews: AI can prioritize risky entitlements and suggest revocations, making recertification cycles more efficient.
- Context-aware decision-making: AI provides contextual insights (e.g., whether a user’s peers hold similar access or if access was actually used).
- Continuous compliance: AI helps maintain least-privilege access dynamically, reducing the chance of audit findings and regulatory penalties.
With AI, governance becomes less of a checkbox exercise and more of an ongoing assurance mechanism.
Adaptive Authentication
The balance between security and user experience is a constant challenge in IAM. AI-powered adaptive authentication solves this by adjusting authentication requirements based on contextual risk signals:
- Low-risk scenarios (familiar device, usual location) may only require a password.
- High-risk scenarios (login attempt from an unusual IP address or device) trigger step-up authentication such as MFA, biometric verification, or behavioral checks.
This intelligent approach reduces friction for legitimate users while maintaining strong security against account takeover attempts.
- Key takeaway
After all advantages we listed, we could say that AI has moved beyond theory – by actively transforming the IAM sphere today. By enhancing automated onboarding/provisioning, smarter identity verification, anomaly detection, operational efficiency, intelligent monitoring and identity analytics, intelligent access governance, and adaptive authentication, AI empowers organizations to build IAM programs that are not only more secure but also more efficient and user-friendly. This means that companies that adopt AI in IAM, will strategically reduce risks, streamline operations, and gain the resilience needed to thrive in the digital economy.
If your organization is looking for a trusted IAM partner to enhance your cybersecurity resilience and support scalable, long-term compliance, don’t hesitate to get in touch with us. We are here to help you turn information security into a true business advantage.

