As technology advances, IT security becomes more critical than ever. Even organizations with strong security frameworks can have hidden vulnerabilities that put sensitive data and business operations at risk. IT audits are an essential tool to identify these weaknesses before they can be exploited.
A structured GAP analysis during an audit helps organizations identify where their security measures do not meet best practices and requirements. It enables targeted improvements that strengthen resilience and reduce risk. By uncovering high-risk security gaps, audits provide a roadmap for strengthening defenses and ensuring regulatory compliance.
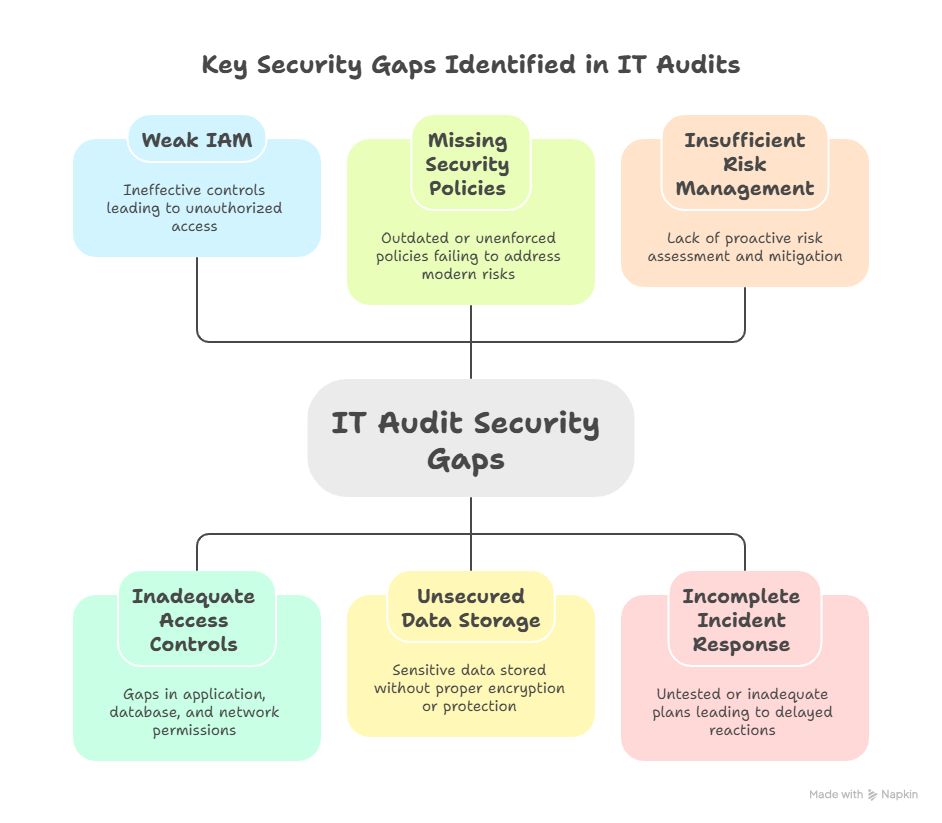
Below are six of the most common and high-impact security issues identified during IT audits – and why addressing them should be a top priority.
1. Weak Identity and Access Management (IAM)
One of the most frequently identified audit issues is ineffective Identity and Access Management. Weak IAM controls often manifest as excessive user privileges, lack of role-based access, shared accounts, or the absence of multi-factor authentication (MFA). These weaknesses increase the risk of unauthorized access, insider threats, and credential-based attacks. Without a structured IAM framework, organizations struggle to enforce the principle of least privilege, leaving critical systems and sensitive data unnecessarily exposed.
2. Inadequate Access Controls
Inadequate access controls go beyond IAM and include weaknesses at the application, database, and network levels. Common issues include poorly configured permissions, lack of segregation of duties, and insufficient monitoring of privileged access. These gaps make it difficult to detect unauthorized activities and can allow attackers – or internal users – to move laterally within systems. From an audit perspective, weak access controls are a red flag for both security and compliance failures.
3. Missing or Outdated Security Policies
IT audits often reveal that security policies are either missing, outdated, or not aligned with current technologies and regulatory requirements. Even when policies exist, they may not be consistently communicated or enforced across the organization. Outdated policies fail to address modern risks such as cloud usage, remote work, and third-party access. This creates gaps between documented controls and actual practices, weakening governance and increasing compliance risk.
4. Unsecured Data Storage
Audits frequently uncover sensitive data stored without adequate protection. This may include unencrypted databases, unsecured cloud storage, unmanaged backups, or legacy systems holding critical information. Unsecured data storage significantly increases the impact of security incidents. If data is not properly classified, encrypted, and protected throughout its lifecycle, organizations face higher risks of data leakage, regulatory fines, and reputational damage.
5. Insufficient Risk Management
A mature risk management process is essential for proactive security – but many IT audits reveal that risk assessments are performed irregularly or not at all. In some cases, risks are identified but not properly documented, prioritized, or mitigated. Without a structured risk management approach, organizations react to incidents rather than anticipating them. This lack of visibility makes it difficult to allocate resources effectively or demonstrate due diligence to regulators and auditors.
6. Incomplete Incident Response Plans
Another critical gap uncovered by IT audits is the absence of a comprehensive and tested incident response plan. Organizations may have informal procedures, but they are often incomplete, outdated, or untested through simulations or tabletop exercises. An incomplete incident response plan leads to delayed reactions, unclear responsibilities, and ineffective communication during a security incident. This can significantly amplify operational downtime, financial losses, and regulatory consequences.
Why Closing Security Gaps Identified in IT Audits Is Critical?
Addressing security gaps identified during IT audits is not just about passing the next audit. It directly strengthens the organization’s resilience against cyber threats, improves operational stability, and builds trust with customers, partners, and regulators.
Proactively closing these gaps helps organizations:
- Reduce the risk and impact of security incidents
- Demonstrate compliance with regulatory and industry standards
- Improve governance, accountability, and transparency
- Align security investments with actual business risks
Ultimately, audit findings should be viewed – not as failures, but as opportunities to improve.
How Can PATECCO support you?
PATECCO helps organizations turn IT audit findings into actionable, sustainable security improvements. Our experts support you across the entire journey – from identifying and prioritizing risks to implementing and optimizing controls.
With PATECCO, you benefit from:
- Comprehensive GAP analysis to identify security gaps and prioritize improvements
- Strategic guidance on IAM, access controls, and security governance
- Support in developing and updating security policies and frameworks
- Risk-based approaches aligned with regulatory and business requirements
- Assistance in designing, testing, and improving incident response capabilities
Still unsure if your IT security is at risk? Discover your vulnerabilities in just 5 days with PATECCO’s GAP analysis.
For more information visit out IT-Security page: https://patecco.com/it-security/
