We live in an increasingly connected world where cyber threats are becoming more sophisticated and persistent. As a result, identity and access management (IAM) has become a critical priority for organizations of all sizes. One often overlooked security vulnerability is the presence of orphaned accounts – user accounts that remain active even though the associated individual has left the organization or no longer requires access. While they may seem harmless, orphaned accounts can represent a significant security risk if left unmanaged.
In this article, we explore what orphaned accounts are, why they pose a threat, and what steps organizations can take to mitigate the risks associated with them.
What are orphaned accounts?
An orphaned account is a user identity in a system that no longer has a valid owner. These accounts typically arise when employees leave an organization, change roles, or when external vendors or partners complete their projects but their access credentials are not deactivated or removed. These accounts often persist across various systems, including Active Directory, cloud platforms, email servers, and business applications.
Why Orphaned Accounts are a security threat
Orphaned accounts can serve as entry points for cyberattacks. Because these accounts are not actively monitored or used, they are often overlooked by security teams – making them attractive targets for threat actors. Here are some of the major risks:
1. Unauthorized Access
Malicious insiders or external attackers can exploit orphaned accounts to gain unauthorized access to sensitive data or critical systems, often without detection.
2. Privilege Escalation
Orphaned accounts that previously belonged to high-level users (e.g., administrators, IT personnel) may retain elevated privileges. If compromised, these accounts can be used to move laterally through the network and escalate access.
3. Compliance Violations
Regulatory standards such as GDPR, HIPAA, and SOX require strict control over user access. The presence of orphaned accounts can lead to compliance breaches, resulting in fines and reputational damage.
4. Audit Failures
Inactive accounts can complicate security audits and increase the likelihood of failing internal or third-party reviews.
Causes of Orphaned Accounts
Orphaned accounts don’t just appear overnight – they are often the result of gaps in processes, communication, or technology. Understanding the root causes behind their existence is the first step toward effectively managing them. From incomplete offboarding to siloed systems and a lack of automation, several factors contribute to the accumulation of these high-risk, unmanaged identities. Identifying these causes helps organizations build more resilient and secure identity management practices.
Several organizational challenges contribute to the proliferation of orphaned accounts:
- Incomplete offboarding processes when employees leave or change roles
- Lack of synchronization between HR systems and IT access controls
- Siloed environments where accounts exist across multiple unconnected systems
- Manual account management that leads to oversight or delay
- Limited visibility into user access rights and activity
- Inconsistent role definitions, making it hard to track and update access appropriately
Identifying these root causes helps organizations build stronger, more secure identity management practices.
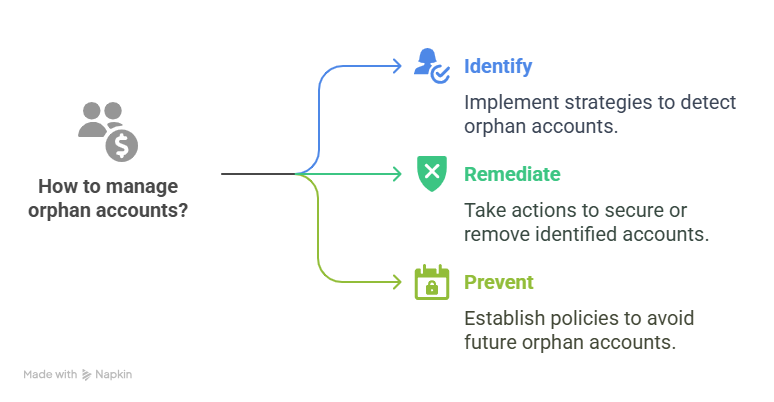
How to detect and eliminate Orphaned Accounts
Once orphaned accounts are identified as a risk, the next challenge is detecting and removing them before they can be exploited. Fortunately, with the right tools and governance strategies, organizations can gain visibility into inactive or unassigned accounts and take action. This section outlines best practices for discovering orphaned accounts, implementing automated controls, and establishing long-term preventive measures to strengthen your organization’s security posture.
Don’t let Orphaned Accounts become a backdoor
Orphaned accounts are a silent yet potent threat lurking in many organizations. They may not grab headlines like phishing or ransomware, but their potential for damage is just as severe – if not more, due to their stealthy nature. By proactively addressing orphaned accounts through automation, strong policies, and regular audits, organizations can significantly reduce their risk posture. In the era of Zero Trust and increasing regulatory pressure, visibility and control over all digital identities are no longer optional – they are essential.
If your organization is seeking a reliable IAM partner with the capability to act decisively and scale effectively, feel free to reach us out at info@patecco.com or call +49 (0) 23 23 – 9 87 97 96 .
