As cyber threats become increasingly sophisticated, the speed and effectiveness of an organization’s incident response capabilities can be the difference between minor disruption and catastrophic damage. Among the many security tools and strategies involved in a mature IR program, Privileged Access Management (PAM) stands out as a foundational control that often goes underappreciated – until an incident occurs.
Privileged accounts are a prime target for attackers because they offer elevated access to critical systems, sensitive data, and security configurations. Whether it’s a ransomware attack, insider threat, or third-party compromise, incidents often involve the abuse or hijacking of privileged credentials. This makes PAM not just a preventive control, but a vital player in detection, containment, and recovery phases of incident response.
This article highlights why PAM matters in incident response, highlighting how it strengthens visibility, accountability, and resilience throughout the incident response lifecycle.
PAM as a preventive control
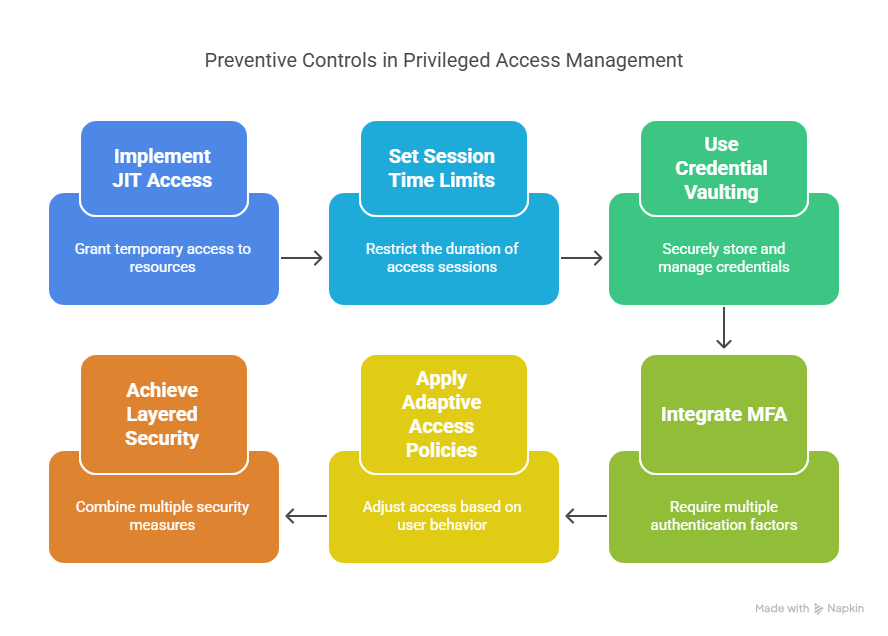
The best incident is the one that never happens – and PAM plays a key role in prevention by minimizing the attack surface. By enforcing least privilege principles, PAM ensures users only have access to the systems and information they need, and only for the time they need it. Features like just-in-time (JIT) access, session time limits, and credential vaulting reduce persistent privileges, making it significantly harder for attackers to find and exploit powerful accounts. Moreover, PAM tools often integrate with multi-factor authentication (MFA) and adaptive access policies, providing layered security that deters unauthorized access even if credentials are stolen.
Strengthening visibility, traceability, and audit readiness
During and after a security incident, one of the most urgent and recurring questions for incident response teams is: “What happened, who was involved, and what was affected?” The ability to answer these questions quickly and accurately is crucial for effective containment, remediation, and regulatory compliance.
Privileged Access Management (PAM) solutions play a central role in delivering this clarity. By providing comprehensive, real-time logging, session recording, and behavioral analytics of all privileged activities, PAM establishes a detailed and tamper-resistant audit trail. This includes actions performed by internal administrators, external vendors, automated services, and even temporary elevated sessions – all of which are commonly targeted during an attack.
This level of traceability empowers security teams to:
- Pinpoint the initial point of compromise
- Reconstruct attacker movements, including lateral traversal and privilege escalation
- Determine exactly which systems, data, or configurations were accessed or altered
- Validate or disprove insider involvement based on recorded behavior
Beyond its value in technical forensics, this evidence is vital for fulfilling legal and compliance obligations. Whether responding to GDPR, SOX, HIPAA, or internal audit demands, PAM provides the reliable documentation needed for post-incident reviews, regulatory disclosures, and executive reporting – ensuring organizations remain accountable, transparent, and audit-ready under pressure.
How PAM Helps isolate and neutralize threats
Once a breach is detected, swift containment is critical to minimize its impact. Privileged Access Management supports this by enabling security teams to quickly revoke access, rotate credentials, block suspicious sessions, and isolate compromised accounts or systems. With centralized control over all privileged access, PAM allows organizations to respond decisively and consistently, avoiding delays caused by fragmented or undocumented administrative access. Additionally, integration with SOAR and SIEM tools enables automated response actions, further accelerating containment efforts.
Supporting recovery and resilience
In the aftermath of an incident, restoring normal operations must be balanced with securing the environment to prevent recurrence. PAM assists in recovery by:
- Enforcing stronger access controls post-incident
- Revalidating privileged account use
- Supporting root cause analysis through audit data
- Helping design more robust access policies
In ransomware cases, for example, PAM helps restore privileged access in a controlled manner, ensuring credentials are not re-used from pre-attack configurations. For compliance-driven industries, PAM also supports documentation efforts required for audits, reporting, and governance reviews.
Integrating PAM into the incident response framework
To fully leverage PAM in incident response, organizations must treat it not as a standalone tool, but as a strategic component of their broader security architecture. This involves:
- Including PAM workflows in IR runbooks and tabletop exercises
- Integrating PAM data into SIEM and SOAR platforms for real-time insights
- Ensuring security teams are trained on using PAM tools during incidents
- Monitoring for anomalous PAM usage as a potential early breach indicator
A well-integrated PAM system not only reacts to incidents but helps detect them early by identifying deviations in privileged behavior – often before traditional indicators of compromise are triggered.
In an era where access equals risk, Privileged Access Management is not optional – it’s essential. Its role in preventing, detecting, and responding to security incidents makes it one of the most valuable investments an organization can make in its incident response strategy. By minimizing risk exposure, enhancing visibility, and enabling swift, informed action during a crisis, PAM transforms privileged access from a liability into a pillar of security resilience. Organizations that recognize this are not only better prepared for incidents – they are also better positioned to build trust, meet compliance demands, and recover stronger from cyber adversity.
If your organization is seeking a reliable PAM partner with the capability to act decisively and scale effectively, feel free to reach us out at info@patecco.com or call +49 (0) 23 23 – 9 87 97 96 .
