The role of key technologies
In an environment of growing cyber threats, regulatory pressure, and expectations for uninterrupted service, global payment technology companies must maintain a secure, resilient, and auditable infrastructure to support digital payment processing. This is the reason why Identity and Access Management (IAM), Privileged Access Management (PAM), and Managed Services have become essential components of modern security strategies.
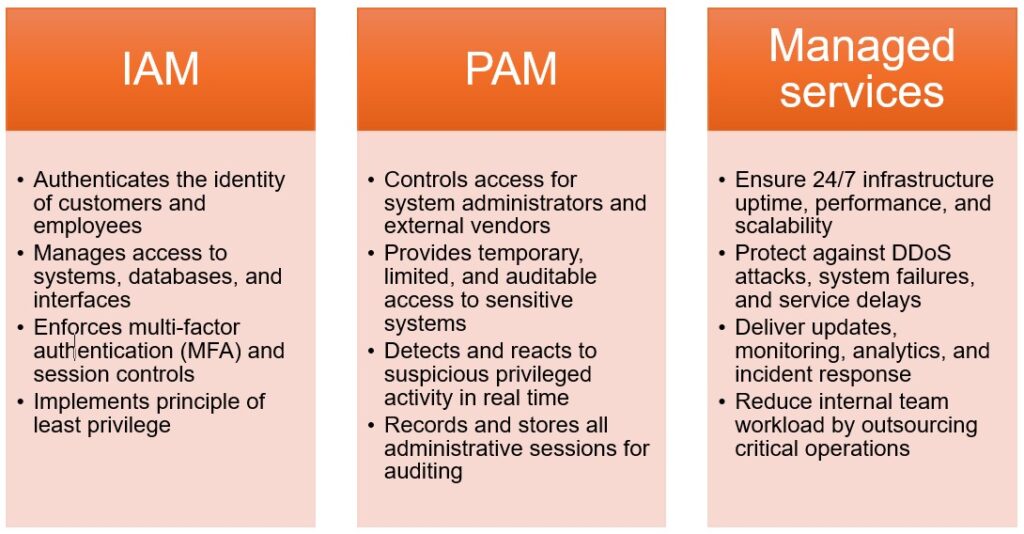
IAM ensures that only authorized users can access critical systems and data, PAM protects and monitors privileged accounts to prevent abuse or breaches, and Managed Services provide ongoing expertise, oversight, and scalability to support 24/7 security operations and compliance requirements.
Real risks without these solutions
Example 1: Compromised employee password
Scenario:
A hacker uses phishing to obtain a username and password of an employee from the transaction approval department. With these credentials, they attempt to access the system and redirect payments.
How IAM helps:
- Multi-Factor Authentication (MFA) prevents access since the hacker lacks the second factor (e.g., token, app, or biometrics).
- Least Privilege Policies limit access even in case of compromise.
- Geo-fencing and IP restrictions detect suspicious login attempts from unknown regions and block them.
Example 2: Misuse of administrative access
Scenario:
A system administrator has full access to the transaction database and decides to manipulate data or exfiltrate information to a competitor.
How PAM helps:
- Just-in-time access with approval: The administrator gains access only after submitting a request and receiving approval.
- Session recording: All actions are logged and can be reviewed.
- Behavioral analytics: PAM detects unusual behavior, such as abnormal database queries or mass exports.
Example 3: DDoS attack or payment platform outage
Scenario:
A financial corporation is hit by a Distributed Denial of Service (DDoS) attack or experiences a critical software bug during peak hours.
How Managed Services help:
- 24/7 monitoring and automated defense from the provider detect and neutralize DDoS threats in real time.
- Scalable cloud infrastructure enables quick traffic rerouting.
- Proactive updates and patches: Maintenance ensures the software lifecycle is secure and vulnerabilities are avoided.
Example 4: Regulatory non-compliance (PCI DSS, GDPR, DORA)
Scenario:
During an audit, the company cannot prove who accessed customer data and when.
How IAM and PAM help:
- IAM provides centralized logs and policies that prove who accessed what, and at what level.
- PAM automatically creates audit trails of privileged user actions.

Kay takeaways
- Without IAM, PAM, and Managed Services, financial services corporations are exposed to serious risks: fraud, regulatory fines, and loss of trust from clients and partners.
- These are not just security tools – they form the foundation of trust, stability, and scalability in digital payments.
- Integrate these technologies into the company’s security and audit roadmap.
If your organization is seeking a reliable IAM partner with the capability to act decisively and scale effectively, feel free to reach us out at info@patecco.com or call +49 (0) 23 23 – 9 87 97 96 .
